 We live in a digital age that has exponentially enhanced our abilities to use technology for virtually everything. I was recently listening to a presentation given by Thomas Friedman, a world-renowned author and commentator that said, “We live in an age where more than 50% of our being is happening in Cyberspace.” What does this mean?
We live in a digital age that has exponentially enhanced our abilities to use technology for virtually everything. I was recently listening to a presentation given by Thomas Friedman, a world-renowned author and commentator that said, “We live in an age where more than 50% of our being is happening in Cyberspace.” What does this mean?
So much of who we are and what we do is happening online. This is how we find information, connect with people, pay for our life, etc. But as Thomas Friedman also pointed out, there are no rules, no protections, no oversights that govern what people do and how they do it in Cyberspace. This has become abundantly clear with how criminals use the information we so naively share.
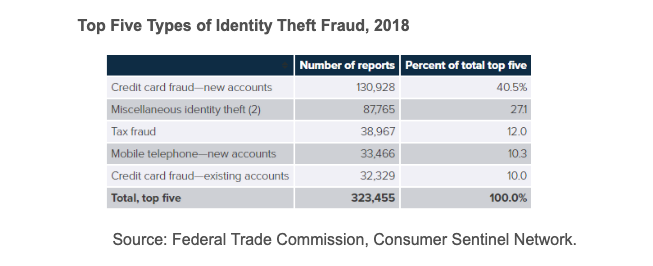
According to 2018 Identity Fraud: Fraud Enters a New Era of Complexity from Javelin Strategy & Research, in 2017, there were 16.7 million victims of identity fraud, a record high that followed a previous record the year before. Below is a chart showing the top five types of Identity Theft:
Here are just a few tips to follow:
Freeze your credit.
If you aren’t actively using your credit, freeze it. You would need to do so with all three credit bureaus. This prevents people from opening any new accounts which would require your credit to be pulled. Here’s a website that explains this process and how to do it:
Read Credit Freeze FAQ's from the Federal Trade Commission
Be careful with information you share over the phone.
Phone scams are on the rise. The IRS, Social Security Administration, credit card companies and your bank, for instance, will never call asking you for your personal information. Chances are also high if you get a phone call that someone you love has been in an accident/situation and needs money immediately, this is fraud. End these calls and always call a legitimate source back to verify.
Watch for mysterious emails.
Be careful clicking on links or downloading attachments received in emails. You should always verify the email address is accurate before doing so, and even then be leery. If you receive email correspondence from a company you know and it’s asking you to do something, call them first just to verify.
Add two-factor authentication.
This security technique is offered as a setting through most of the main services people use (i.e. Apple, Google, Office 365, Yahoo, Facebook, major bank branches, etc.). When logging in online you will be required to not only put in your username and password but also a special code sent to your mobile device. Typically once you log in on one of your known devices you won’t be required to do this every time. But if someone steals your username and password and tries to log in from an unknown device they wouldn’t be able to without your cell phone.
Be careful with public Wi-Fi.
Public Wi-Fi is a blessing and a curse. These aren’t secure networks which means anyone can use them. Hackers can easily get sensitive information from people using public Wi-Fi. So to be safe, never use public Wi-Fi to access personal information (i.e. bank accounts, email, etc.). Instead, consider using your Personal Hotspot if you have one through your phone carrier.
Credit monitoring.
It’s always important to monitor your credit, especially if it’s not frozen. You can do this in one of two ways. Pay for a credit monitoring service, like Identity Guard or Life Lock which does daily monitoring of any credit activity with the three credit bureaus OR you can check your credit report with each credit bureau once per year. The monitoring services are usually $10-$20/month. If you’re a Costco member they have discounted pricing with Complete ID. If you don’t want to pay for credit monitoring you can check your credit report each year at www.annualcreditreport.com (you can space it out by checking with one credit bureau every few months instead of doing all three at one time).
If you suspect your information has been compromised from a Data Breach, here are some action steps.
At this point it’s not IF, but WHEN will we be a victim of identity theft. The more we can proactively be cognizant of this, the quicker we can detect it and take action. As the digital age continues to progress, stop and think about what information you’re sharing online and how protected that information is or isn’t. Form new habits that add a certain shield of protection. As my husband always reminds me, “you shouldn’t live in fear, but you should always be aware and ready.”




